dig Command
The dig command is an excellent tool to test and troubleshoot DNS record changes. There is a Solutio server you can connect to for easy access to dig and this guide will show you how.
Accessing the Server
Follow these steps to setup a tool for connecting to the DNS Tools server. The first four steps are only needed for the initial setup.
1) Download PuTTY
The best terminal for connecting to the server on Windows is PuTTY, which you can download from this page. You want putty.exe listed under the Alternative binary files section. You can place the file anywhere and just run it, no installation needed.
2) Set the Username
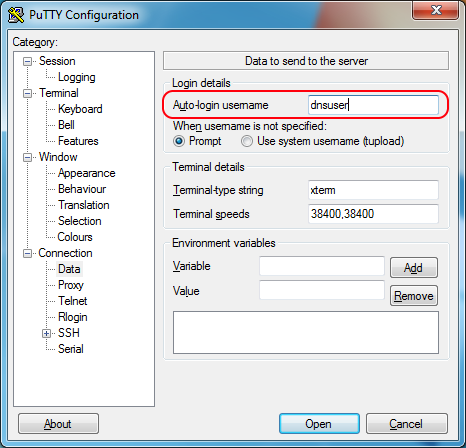
Run PuTTY and navigate to the Connections->Data category on the left side. Set the Auto-login username to dnsuser.
3) Configure the Private Keyfile
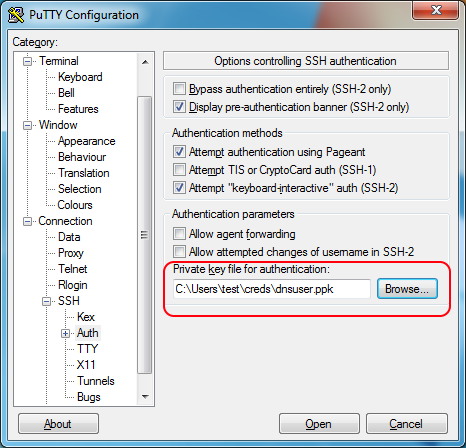
Next, navigate to the Connection->SSH->Auth category on the left side. Click the Browse button and select the dnsuser.ppk file you were given.
4) Set the Remaining Connection Details
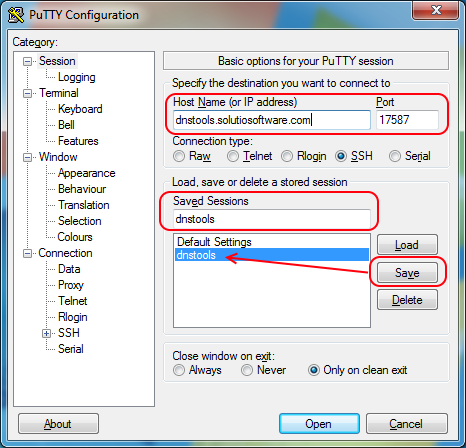
Finally, navigate to the Session category on the left side. In the Host Name field, enter dnstools.solutiosoftware.com. In the Port field, enter 17587. In the Saved Sessions field, enter dnstools. Now click the Save button. After clicking save, dnstools will be listed under the Default Settings in the list box. Every time you launch PuTTY from this point forward, the saved session will appear in the list box.
5) Connect
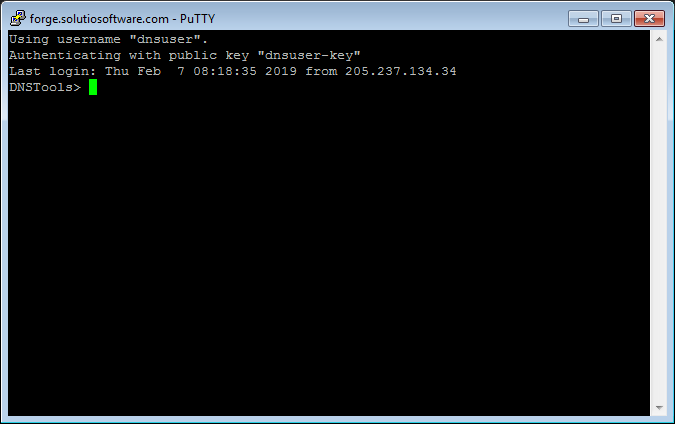
Simply double-click dnstools in the Saved Sessions list box. A mostly black terminal window will appear and look similar to below. Congratulations, you are now connected to the DNS Tools server!
On the first connection you will receive a Putty Security Alert popup, just click the Yes button.
PuTTY Tips
Copy & Paste
The PuTTY terminal works differently when it comes to copy and paste. The standard short-cut keys (CTRL+C, CTRL+V) do not work as expected. Instead, to paste into the terminal, simply right-click. To copy from the terminal, just select the text with the mouse and it is automatically copied to the clipboard. Very efficient!
Command History
You can use the up arrow key on your keyboard to cycle through your previous commands instead of having to re-type them each time.
Server Commands
There are two commands you can use once connected to the DNS Tools server:
dig- Queries DNS records, described below.exit- Disconnects from the server and closes the terminal window. Use this when you are done querying records for the day.
Intro to Dig
Simple Query
dig will query the DNS record for a given domain and record type. If you don't specify a record type, it will look for an A record by default. For example, running dig solutiosoftware.com will produce something similar to this:
DNSTools> dig solutiosoftware.com
; <<>> DiG 9.9.4-RedHat-9.9.4-72.el7 <<>> solutiosoftware.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 51933
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;solutiosoftware.com. IN A
;; ANSWER SECTION:
solutiosoftware.com. 60 IN A 104.130.74.156
;; Query time: 2 msec
;; SERVER: 172.30.0.2#53(172.30.0.2)
;; WHEN: Thu Feb 07 08:35:27 CST 2019
;; MSG SIZE rcvd: 64
The ANSWER SECTION has the resulting IP address.
Go ahead and try it, there is no harm in querying DNS records!
Query for a Certain Record
To query a specify record type, put it before the domain name. For example, to lookup the MX records for Solutio, use the following:
DNSTools> dig MX solutiosoftware.com
; <<>> DiG 9.9.4-RedHat-9.9.4-72.el7 <<>> MX solutiosoftware.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 36609
;; flags: qr rd ra; QUERY: 1, ANSWER: 7, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;solutiosoftware.com. IN MX
;; ANSWER SECTION:
solutiosoftware.com. 60 IN MX 20 alt2.aspmx.l.google.com.
solutiosoftware.com. 60 IN MX 30 aspmx2.googlemail.com.
solutiosoftware.com. 60 IN MX 30 aspmx3.googlemail.com.
solutiosoftware.com. 60 IN MX 30 aspmx4.googlemail.com.
solutiosoftware.com. 60 IN MX 30 aspmx5.googlemail.com.
solutiosoftware.com. 60 IN MX 10 aspmx.l.google.com.
solutiosoftware.com. 60 IN MX 20 alt1.aspmx.l.google.com.
;; Query time: 2 msec
;; SERVER: 172.30.0.2#53(172.30.0.2)
;; WHEN: Thu Feb 07 08:41:09 CST 2019
;; MSG SIZE rcvd: 224
Less Cluttered Output
The +short option will clean up the output considerably:
DNSTools> dig +short CNAME www.diobelle.org
dio-bell.w.solutiosoftware.net.
Querying a Specific Server
By default, the dig command will use the server's configured DNS resolvers (Rackspace). However, you can query any publicly available DNS server with the @ symbol followed by the DNS server. Let's use Google's public DNS to lookup the SEAS text records:
DNSTools> dig +short @8.8.8.8 TXT seaswichita.com
"v=spf1 a include:_spf.google.com ~all"
Since most DNS queries are cached based on the TTL, this can be extremely useful for directly querying a domain's authoritative nameservers, to check if the client has performed the needed DNS updates. For example, let's directly check Serra-KC's domain. First, find the domain's nameservers:
DNSTools> dig +short NS serrakck.org
ns09.domaincontrol.com.
ns10.domaincontrol.com.
TIP:
*.domaincontrol.comnameservers are GoDaddy's,*.worldnic.comare Network Solution's, and*.dnsmadeeasy.comare Solutio's.
Now we'll use one of the nameservers listed to directly query their www subdomain:
DNSTools> dig +short @ns09.domaincontrol.com. CNAME www.serrakck.org
serra-kc.w.solutiosoftware.net.
